I LOL when a customer asks “Can you just…” or “It has to be at no cost”. Really? #DIY.
Author Archives: steve
Note to self when using Sempress theme
If using Sempress WordPress theme, then remember that the ‘Aside’ and ‘Status’ Post Formats do not show the title of the post in WordPress.
This is intended behaviour. This post, incidentally, was an ‘Aside’.
That was a public information broadcast. 🙂
For more info, see this issue: https://core.trac.wordpress.org/ticket/24011?cversion=0&cnum_hist=43
Note to self when using Sempress theme #indieweb …
Note to self when using Sempress theme #indieweb #sempress #wordpress
If using Sempress WordPress theme, then remember that the ‘Aside’ and ‘Status’ Post Formats do not show the title of the post in WordPress. This is intended behaviour. This post, incidentally, was an ‘Aside’. That was a public information broadcast. 🙂 …
Sadly the macOS reinstall has been brewing for …
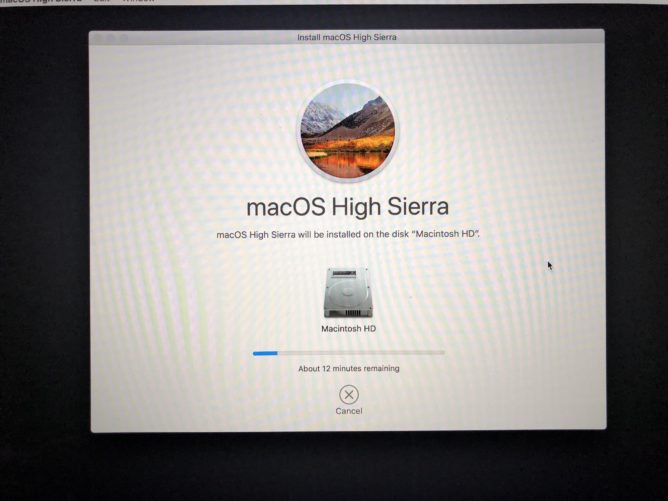
Sadly the macOS reinstall has been brewing for some time.
Of course, it’s remotely possible I could learn …
Of course, it’s remotely possible I could learn something new, too.
Stop application windows snapping to full screen |
Do you have an issue with moving a window by dragging it across the screen and it suddenly snapping (automatically maximizing) to full screen? If so, you let the top of the window touch the top of …
Of course, it’s remotely possible I could learn …
Of course, it’s remotely possible I could learn something new, too.
Stop application windows snapping to full screen | …
Stop application windows snapping to full screen | #linux #MATE
Do you have an issue with moving a window by dragging it across the screen and it suddenly snapping (automatically maximizing) to full screen? If so, you let the top of the window touch the top of … Source: Stop application windows snapping to full screen…
http://dowe.uk/stop-application-windows-snapping-to-full-screen/
Android: https://play.google.com/store/apps/details?id=org.thoughtcrime.securesms&hl=en_GB iOS: https://itunes.apple.com/gb/app/signal-private-messenger/id874139669?mt=8 #deleteFacebook #security #privacy #encryption …
Android: https://play.google.com/store/apps/details?id=org.thoughtcrime.securesms&hl=en_GB
iOS: https://itunes.apple.com/gb/app/signal-private-messenger/id874139669?mt=8
#deleteFacebook #security #privacy #encryption #friendstrustfriends
