Linux is so powerful, sometimes I wonder how it can possibly juggle some serious I/O with such limited resources (Core i7 2640M, 16GB).
Linux is so powerful, sometimes I wonder how …



Linux is so powerful, sometimes I wonder how it can possibly juggle some serious I/O with such limited resources (Core i7 2640M, 16GB).
Here’s the deal:
1)You have no time and you want to try the latest Fedora release because it looks pretty darn good.
2) You accept the default disk partitioning scheme which the kind people at Red Hat / Fedora project set up for you, because they only have your best interests at heart, right?
3) While using this cutting-edge release, something nasty happens like, ooh, perhaps a sound driver locks up the entire system and you have to hard-reset the machine (that is, switch it off by the power switch because nothing responds to input).
What next? If, like me (on one occassion) you try to boot up the machine and get no further than the recovery console, you’d feel a bit aggravated. But there is an alternative – do a disk check. You may have read my verbose coverage for How to do a disk check in Linux before. This takes it one step further – how to check your logical volume when it’s encrypted and formatted using the latest ext4 filesystem.
Instead of the method used before, this time I booted from a Live CD. You can find one to download at the Fedora project. Ensure that this CD matches the release of the version you are trying to recover. In this case, that’s Fedora 10.
Once you have booted the offending machine up with the Live CD, open up a terminal by pointing to Applications > System Tools > Terminal. Once in the terminal window, just type:
# su
…to become the root user. This is essential to using all the disk tools.
You may be tempted to check for volume groups first:
# vgscan
.. but this would return nothing.
What’s happening here is that the Volume Group, located on that partition, is itself encrypted. Once unlocked, you can then gain access to both of the Logical Volumes – the swap volume and the root (/) volume.
To unlock the encrypted Volume Group, first you need to establish which partition it resides on:
# fdisk /dev/sda
The number of cylinders for this disk is set to 12161.
There is nothing wrong with that, but this is larger than 1024,
and could in certain setups cause problems with:
1) software that runs at boot time (e.g., old versions of LILO)
2) booting and partitioning software from other OSs
(e.g., DOS FDISK, OS/2 FDISK)
Hit p to print the partitions on your primary disk:
Command (m for help): p
Disk /dev/sda: 100.0 GB, 100030242816 bytes
255 heads, 63 sectors/track, 12161 cylinders
Units = cylinders of 16065 * 512 = 8225280 bytes
Disk identifier: 0xb07eb07e
Device Boot Start End Blocks Id System
/dev/sda1 * 1 5377 43190721 7 HPFS/NTFS
/dev/sda2 5378 5402 200812+ 83 Linux
/dev/sda3 5403 12161 54291667+ 8e Linux LVM
So the partiton of type “Linux LVM” (Logical Volume Managed) is the baby we’re after.
To unlock the encrypted Volume Group, use the following:
# cryptsetup luksOpen /dev/sda3 mydisk
This sets up the encryption/decryption kernel subroutines to allow access to device /dev/sda3, mapped to a device node called “mydisk” in /dev/mapper/ . We’ll not actually need to use this device node, but it could be handy to know if you needed to perform further diagnostics.
You will be prompted to enter the encryption key which is stored in one of eight “slots” on the disk. If the key you enter matches a key in any slot, your disk will become unlocked. Assuming that it is, you can then scan once again for Volume Groups:
# vgscan
Reading all physical volumes. This may take a while...
Found volume group "VolGroup00" using metadata type lvm2
Now we’re getting somewhere. Let’s activate the VG and display the LVs (Logical Volumes) it contains:
# vgchange -a y
2 logical volume(s) in volume group "VolGroup00" now active
# lvdisplay
--- Logical volume ---
LV Name /dev/VolGroup00/LogVol00
VG Name VolGroup00
LV UUID RE7t2h-nIy9-dWZ9-xt26-Fgq4-gFd8-34E3f2
LV Write Access read/write
LV Status available
# open 0
LV Size 47.81 GB
Current LE 1530
Segments 1
Allocation inherit
Read ahead sectors auto
- currently set to 256
Block device 253:3
--- Logical volume ---
LV Name /dev/VolGroup00/LogVol01
VG Name VolGroup00
LV UUID B7XJzD-9sS0-3iHx-AWBE-W9qN-TvRb-vCdYZF
LV Write Access read/write
LV Status available
# open 0
LV Size 3.91 GB
Current LE 125
Segments 1
Allocation inherit
Read ahead sectors auto
- currently set to 256
Block device 253:4
We can deduce from the sizes of these two volumes that the first of the two is the root (/) volume, and the second is the swap volume.
As the purpose is to FIX the filesystem on it, which may have become corrupt through the hard-reset performed earlier, we do not want to mount this volume. Instead, as we now have a device node for this activated volume, at /dev/VolGroup00/LogVol00, we can simply perform a disk check straight on it.
To check which extn file system checking tools are on the system, you can tab-complete at the command line:
# fsck.(hit tab)
fsck.cramfs fsck.ext3 fsck.ext4dev fsck.vfat
fsck.ext2 fsck.ext4 fsck.msdos
As this was formatted an ext4 volume, that’s what we use:
# fsck.ext4 /dev/VolGroup00/LogVol00
esfsck 1.41.3 (12-Oct-2008)
/dev/VolGroup00/LogVol00: recovering journal
Clearing orphaned inode 730 (uid=0, gid=500, mode=0100600, size 2263160)
Clearing orphaned inode 187182 (uid=500, gid=500, mode=0100600, size 4096)
... and so on until ...
/dev/VolGroup00/LogVol00: clean, 190926/3137536 files, 2016683/12533760 blocks
Now there are two more steps to perform: de-activate the volume group, and lock the encryption of the drive.
# vgchange -a n
0 logical volume(s) in volume group "VolGroup00" now active
# cryptsetup luksClose mydisk
The second command returns nothing, which means it did not error (the disk is now encrypted and not writable-to without unlocking again).
I hope that helps someone with a sense for adventure but not enough time on their hands for when things go somewhat awry!
Fedora 16 is here. With all GNU/Linux distributions, newer versions generally mean better hardware support, usability and so on. Unfortunately, for users of netbooks, laptops and basically any hardware that contains Realtek’s 8192e wireless chip, things can still be problematic.
I posted, previously, a rather kludgy solution to fixing this in Fedora 14. Then 15 came along, and the fix I was using then no longer worked. This is because my previous solution installed the Linux kernel staging drivers for a kernel version very similar to that running in Fedora 14 (but actually built for Ubuntu).
Now that we are 2 versions of Fedora down the road (12 months, then), is the situation better for the humble RTL8192e_PCI ? Sadly, no. The main problem is that the 8192e driver is still in the Linux driver staging tree rather than in the main code line. In the respected opinion of the Linux kernel developers and testers, this means the code isn’t good enough to be enabled by default. Quite when it will be “ready” to hit the trunk, I’m not sure.
In the meantime, this means you have to install the kernel’s development modules (staging drivers).
This is quite simple in Fedora:
# yum install kmod-stagingThis problem has been reported for other systems – Jayway covers 64-bit Ubuntu, which is where I derived most of the info I needed (thanks guys!).
If you are developing Android apps using Eclipse, especially on 64-bit Fedora 16, then you too may have come across the error message:
Failed to get the adb version: Cannot run program "/home/[user]/[path] /android/[sdk] /tools/adb": java.io.IOException: error=2, No such file or directory
I did.
To fix it, you need to install 32-bit compatibility libraries. On Ubuntu (and probably Debian) you can use the getlibs tools. For Fedora users, it requires installing a few bits and pieces. Easily accomplished with this:
su -
yum install libstdc++.i686 ncurses-libs.i686
compat-libstdc++-33.i686
Yum will pull in the necessary dependencies.
Restart Eclipse and the error should disappear.
 |
| ThinkPad T420. Shiny and new. |
It is with incredible reserve that I discuss my new Lenovo ThinkPad T420, such is my excitement. As a natural born geek, software developer and sysadmin, there is something about a ThinkPad which is “just right”.
The lure of a ThinkPad is unquestionable. It’s the promise of your best bit of code ever. It’s the idea that it’ll be with you for years; your faithful companion. It’s the reassurance of industry-leading build quality and top-spec engineering, using high quality components. But it’s more than that too. It’s an identity, a bit like that of Apple users – but thankfully in more self-respecting way. You have a ThinkPad, you join an elite. It’s everything you want.
You want this so badly that it comes as a bit of a surprise when all is not quite what it seems.
 |
| Branded accessories – one of those indulgences. |
Better the devil?
As Lenovo only offer such spiffing hardware bundled with a throwaway operating system, you must suffer the wasted hours and ridiculous horseplay that ensues from such choices being made for you. We are all too familiar with this scenario… so, I’ll continue!
Here is my experience, abridged:
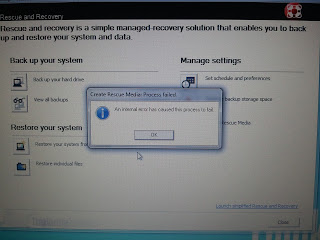 |
| Creating recovery media fails. Classic. |
Not to be
So far, any reasonable, sane person would not feel very confident using Win7 on this machine. The dream probably wouldn’t be shattered, but clearly the software configuration is dysfunctional, ignoring user preferences and showing some worrying reliability issues out of the box.
Luckily, being part of an elite means that you don’t follow the masses. The throwaway software, bundled with the machine, is designed for people who don’t, won’t or can’t think. It’s also designed for those who blythely accept it, probably “because it’s safer”. Well, luckily for Windows users it must be a lot safer now that Norton is installed, regardless of your wishes! Phew!
To be
| Fedora 16 live CD, running on this T420. |
The alternative, as always, is to not accept what you are given. Instead, seek a better solution that you can feel confident in. For this ThinkPad T420, the better solution is GNU/Linux, Fedora 16 flavour.
Here is how easy Fedora is:
But don’t take my word for it, try it yourself.
If, that is, you have the mind to.
So, this is what I’m doing today (from left to right):
2) Fixing a grub/mbr bootloader on netbook
3) setting up file server
5) answering emails and ordering an ssl certificate.
I LOVE quiet days in the office! 🙂
/lib/ld-linux.so.2 missing? libXext.so.6 can’t be found?
I recently [at the original time of writing] installed Fedora 11 [x86_64] on a test machine, to see how the development desktop build of my favourite Linux distribution is doing – and it’s very nice indeed.
I tried to install Zend Studio 5.5 and soon came across problems, which I found out related to not having 32-bit versions of Xorg and glibc installed. To remedy this, ensure you follow these steps:
su -c 'yum groupinstall Java'
su -c 'yum install glibc.i686 libXext.i586'
Once installed, I was able to fire up the Zend Development Environment:
/usr/local/Zend/ZendStudio-5.5.1/bin/ZDE
.. and it was running on the native (OpenJDK) 64-bit JAVA runtime! How’s that for progress!
(to view all photos in this article, visit my flickr photoset)
I’ve been needing a netbook for work for a little while. So, chancing upon Martin Lewis‘s wonderful MoneySavingExpert web site, this article on cheaper netbooks was the prompt I needed.
My main criteria for a netbook were:
Given that nearly all early (pre dual core) netbooks are based on Intel’s Atom / 945 mobile chipset, most of the above criteria were already met. Ergonomically, I’d read that each netbook had its foibles, so this point was moot. The battery life was, for me, the deciding factor, which is why I chose a Samsung N130: the only model in the discounted range which ships with a 6-cell battery. In ideal circumstances, this will last 6 hours.
Order process, shipping, packing and unpacking
The Argos outlet on eBay accepted only PayPal payments, but this didn’t matter to me. The purchase process was as painless as you could expect. I ordered the unit on a Friday morning. On a Monday morning, at my office, it arrived courtesy of a cheery DHL delivery chap. No complaints so far!
The packing itself was as you’d expect: satisfactory for the job, with nothing much else to note. Unboxing the unit was a quick affair, and before long I had a shiny netbook on my desk. Considering this unit is classed as “refurbished”, I could see absolutely no defect or mark on it whatsoever. I would have been very happy were this brand new.
Plugging in, powering on, first impressions
When unpacking the device, I was impressed with the general feel of it. The plastic shell feels robust and the lid action is smooth. Instead of a clasp, the lid clamps to the base by means (I’m guessing) of a magnet arrangement, which has a lovely feel about it. Furthermore, Fedora behaves as expected, going straight into standby when the lid is closed.
The weight of the unit was good too. Before I put the battery in, that is. After that, the weight felt subjectively like it had more than doubled, which would put some people off I’d imagine. However, it’s hardly as heavy as my laptop so by my standards it’s still very light. A positive effect of the battery unit is in providing more stability while on a desk, and more resistance to the motion of closing/opening the lid. All together, it works well.
Along the front, left of the touchpad, are 5 LEDs. I question the value of having an “on” LED in addition to a “charging” LED, but these are tiny devices so power consumption is likely to be equally tiny. Besides, if unplugged, the charging LED isn’t illuminated. Again, another moot point.
The feel of the keyboard is good. There isn’t a compromise in terms of key press action, although to fit in a full QWERTY keyboard, some compromises in layout have had to take place. As you can see, the hash (#)/tilde and right square-bracket/brace keys are squashed in, but the compromise is acceptable.
Fedora installation and general usage
 I use Fedora, CentOS and Red Hat in my day job, so for me it’s the architecture that I prefer due to familiarity (which, in this case, has not yet bred contempt!).
I use Fedora, CentOS and Red Hat in my day job, so for me it’s the architecture that I prefer due to familiarity (which, in this case, has not yet bred contempt!).
Using the usblive-creator tool in F13 on my laptop, I was able to set up a USB drive with a Fedora 12 live CD image, ready to boot and install on the netbook. I’d opted for F12 because I’ve had issues with mobile broadband on F13 that worked fine on F12, and mobility is the primary goal here. A quick change to the boot order in the BIOS and it was good to go.

I was surprised how quickly the installation completed. After having read about Atoms generally being slow processors, I’d expected an unhealthy dose of lethargy when installing the OS. The first boot wasn’t particularly tardy either (and this is running on a 160GB Toshiba hard drive with Fedora’s default encrypted LVM set up). It’s comparable to my HP laptop (2007 model) with a Turion TL-60 (@2GHz) w/4GiB RAM (@667MHz). In usage, though, it’s somewhat slower than the AMD laptop, taking considerably longer to load up Firefox (with half as many extensions, too).
As hoped, my Huawei E270 mobile broadband dongle worked straight away. I was also pleased that the webcam worked with no effort whatsoever (screenshot shows Cheese; ’nuff said)! So, what doesn’t work straight away?
A bit more on ergnomics
It has taken me a little while to get used to the layout of the keyboard and touchpad. A problem I am overcoming slowly is that the touchpad’s two buttons are actually a single, rocker-style button. It sits flush to the surface of the base, and this lack of tactile feel I find awkward. I often find my thumb in the wrong position, mistakenly pressing on the bottom of the touchpad rather than the left button. The pointer then jumps across the screen instead of clicking on the intended widget. A small but annoying issue.
Also, the keyboard is great to use while typing (as I do here, writing this review on the N130) but for cursor positioning it can become more tricky. Hitting CTRL-End to position the cursor at the end of some text, for example, is now CTRL-Fn-PgDn(End), given the multi-function aspect of the PgDn(End) key. Likewise, the cursor keys are just a shade on the small side. But these are minor complaints in the overall picture.
Final analysis
Taking into account the annoyances, weighing them against the needs of the many… I would have to have to award this machine 8/10. At £150 (incl VAT) + £4 postage, it has exceeded my expectations. Sure, it’s not perfect, but the price, utility and solid build get my vote. I would recommend one for a partner, friend or colleague….. maybe even a parent 😉
Oh, there is one thing about it that I couldn’t understand. There was this sticker on the top which made no sense (“Designed for Windows XP”). Surely you design an operating system for target hardware and not the other way around..? Well, regardless, I think the new location for the sticker makes much more sense. 🙂
new ->
Short one today – I was looking for a way of converting all my ripped CDs to an alternative format for portable audio use.
Here’s a useful link for doing scripted, recursive audio format conversion.
Now you can rip all those CDs to FLAC format (which is lossless, unlike lossy mp3 – CBR or VBR) and then convert the lot to mp3 for the iPod, car, etc.
Oh, and a copy of Fedora or Ubuntu would probably be handy too 😉
Of course, you could pay for a commercial alternative or even – heaven forbid – “upgrade” your iTunes for DRM-de-restricted AAC files (which are still lossy-format files anyway).
So, why bother, when a CD costs the same and has better sound quality?
Forget digital downloads, until they respect your freedom. Buy CDs!!
Or, if you are 100% sure your data will always be safe and/or don’t have a hi-fi CD player (in addition to CD/DVD-ROM drive) to justify getting physical media, investigate these forward-looking alternatives:
Enjoy!
I’ve decided to catalogue my experience with Fedora 9. The reasons for this are:
So, what first?
I plan to record my experience of installing Fedora 9 on my blog so that people who are considering switching to Linux, or switching from another distribution to Fedora, can decide what the benefits might be. It’s also going to serve as a reference for myself, so I can see why it’s such a good/bad idea to do it again!
Finally, I have gained so much by simply being interested in Open Source software, that I felt it was about time to give something back. As an English graduate, documentation is probably the best thing I can start with. I hope it’s of help to someone!