The problem: you cannot boot a paravirtualised machine from a CD-ROM for the purposes of installing a virtual machine. You may also be on a wireless link set up by NetworkManager and WLAN0 isn’t a bridged interface.
Here’s the solution:
- Download the ISO of your favourite distro and burn to DVD, then mount on your machine (this will probably happen just by inserting the disc on your drive). If a window opens in your desktop, highlight the path in the address bar and copy it to the system clipboard (CTRL-C).
- Install Apache and start the apache/httpd service
- In /var/www/html (/var/www on debian, I believe) simply create a symbolic link to the directory where the DVD is mounted. In this example, I am using CentOS:
# ln -s /media/CentOS_5.4_Final/ centos - Now create the virtual machine, by starting up virt-manager, ensuring that it can connect to Dom0 and select New…
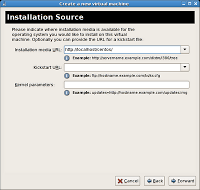
- In the Installation Source section of the virtual machine creation dialog, specify the following parameter: Installation media URL: http://localhost/centos (the path to the installer repository)
- In the “type of network” selection, select Virtual Interface.
- Click through the rest of the set up – but BEFORE YOU COMPLETE IT, GET READY TO PAUSE THE VM. The virtual machine will start up automatically when you finish the set-up steps.
- As soon as you start the VM, the initial bootstrapping files should load and the distribution’s kernel should start up. Only when the console window opens should you pause it!
- If you are using CentOS, you now need to modify the configuration file that’s been created, following these steps:
- Download the Xen kernel and initial ramdisk from here: http://mirror.centos.org/centos/5/os/x86_64/images/xen/ (change the path if you’re using an i386 host)
- Save them somewhere sensible: I made /var/lib/xen/boot and put them in there.
- Un-pause and Shutdown the virtual machine.
- Modify the config file, to include the paths to the xen-aware kernel and initrd (put these entries at the top, adjusting for your path as necessary):
kernel = "/var/lib/xen/boot/vmlinuz" ramdisk = "/var/lib/xen/boot/initrd.img" - IMPORTANT – also comment out the line for pygrub, so:#bootloader = “/usr/bin/pygrub”
- Save the config and run the virtual machine. Nearly there! Now open up the console to the virtual machine…
# ifconfig wlan0(substistute eth0 for wlan0 if you’re using a wired ethernet connection)
The installer should then run through the rest of the motions and voila – a paravirtualized virtual machine installed from local CD/DVD-ROM.
When the installer has finished running, uncomment the pygrub line in the config file.
If you spot any errors with this process, please let me know so I can correct the procedure.
Happy Christmas! *<(:-##