http://www.theverge.com/2016/3/6/11168718/ray-tomlinson-dead-inventor-of-email-obituary
Ray Tomlinson passed away Saturday. What a legacy to leave.

http://www.theverge.com/2016/3/6/11168718/ray-tomlinson-dead-inventor-of-email-obituary
Ray Tomlinson passed away Saturday. What a legacy to leave.
Scammers rely on your ignorance in order to fool you into clicking on their link and typically entering your bank details.
Don’t let them!
DISCLAIMER: DO NOT TRY TO VISIT THE EXAMPLE SCAM LINK GIVEN IN THIS POST. YOU ALONE ARE RESPONSIBLE FOR YOUR ACTIONS.
When you receive a link in an email, you should analyse that link to determine the authenticity and legitimacy of that link, before you click on it.
I was recently forwarded a scam email to analyse. If you have recently received a suspicious email with a link, here’s how to analyse that link.
Firstly, hover the mouse pointer over that link. At the bottom of your email window (commonly called the status bar), you should see a web address appear.
In this example, a link was received purporting to be from the UK bank Cahoot. But the link address is suspicious – so let’s analyse it…
http://ip270-c6.gi.digl.pl:8887/securebank.cahoot.com/servlet/com.aquariussecurity.bks.security.authentication.servlet.LoginEntryServletBKS/
… the bit in bold is what you’re interested in. The rest is not really of interest. However, when you come to inspect a link in the future, it’s worth knowing the following:
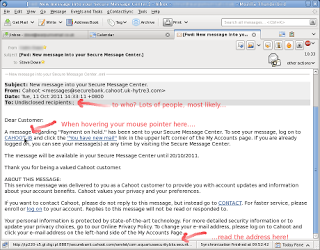 |
| How to analyse a link in Thunderbird (click for larger image) |
This means the protocol that your browser will use. A secure, encrypted browser connection begins https:// ; therefore, the link above will be unencrypted (not secure) between your computer and the server. This is a tell-tale sign that it’s trouble.
This is the domain name, like “bbc.co.uk“, “fedoraproject.org” and “google.com“. This is the most important bit. The best way to read this is actually from right to left. The most right hand part, “pl“, is the top-level domain (TLD). pl is the TLD for Poland. tw is the TLD for Taiwan. ru = Russia. And so on. For reference, you can find a list of TLDs here: http://en.wikipedia.org/wiki/List_of_Internet_top-level_domains
The next two bits should really indicate the organisation of the originating email. digl is meaningless; it’s been made up by a scammer to probably infer “digital” or something like that. Likewise, gl is also meaningless.
A meaningful alternative would be cahoot.co.uk, as it is registered with a UK TLD and represents the claimed originator of the message.
The last bit of this link is what’s called a port number. The (optional) use of this by scammers is again a visual distraction which makes it harder to read the real web address. Apart from the fact that no bank would ever request your details by email anyway, if they were credible they most certainly wouldn’t use a web address with a non-standard port number.
The best thing to do when reading an address is to ignore the port number but be aware of the fact that it’s been used.
For more information, check out this PDF on avoiding email scams.
And for those who were paying attention and spotted the deliberate mistake, well done! 🙂