Android: https://play.google.com/store/apps/details?id=org.thoughtcrime.securesms&hl=en_GB
iOS: https://itunes.apple.com/gb/app/signal-private-messenger/id874139669?mt=8
#deleteFacebook #security #privacy #encryption #friendstrustfriends

Android: https://play.google.com/store/apps/details?id=org.thoughtcrime.securesms&hl=en_GB
iOS: https://itunes.apple.com/gb/app/signal-private-messenger/id874139669?mt=8
#deleteFacebook #security #privacy #encryption #friendstrustfriends
A tweet was recently posted featuring an advert claiming Firefox is the better browser in terms of respect for privacy:
Shots firedfox pic.twitter.com/yaKS2hwOyS
— Kit (@meatcomputer) July 2, 2017
Sadly, this isn’t the case, as this Pale Moon update clearly describes:
https://forum.palemoon.org/viewtopic.php?t=16154&p=117375#p117375
So, if you use #Firefox, best to expect information leakage back to #Google anyway. If you value your privacy and want a functional browser, check out Pale Moon!
Use Firefox? Best to still expect information leakage. #bigbrother #internet #privacy #security
A tweet was recently posted claiming Firefox is the better browser in terms of respect for privacy: Shots firedfox pic.twitter.com/yaKS2hwOyS — Kit (@meatcomputer) July 2, 2017 Sadly, this isn’t the case, as this Pale Moon update clearly describes:…
UK Gov reaches an all-time low as it tries to monitor everyone.
https://www.theregister.co.uk/2017/05/04/uk_bulk_surveillance_powers_draft/
Protect yourself now, with Signal (iOS/Android). (Intro Video)
Mass-surveillance just took another step forward. :( #freesoftware #privacy #security
UK Gov reaches an all-time low as it tries to monitor everyone. https://www.theregister.co.uk/2017/05/04/uk_bulk_surveillance_powers_draft/ Protect yourself now, with Signal (iOS/Android). (Intro Video)
UK Snoopers' Charter gagging order drafted for London Internet Exchange directors #privacy&security #security
UK Snoopers’ Charter gagging order drafted for London Internet Exchange directors. http://www.theregister.co.uk/2017/02/17/linx_snoopers_charger_gagging_order/ Sinking to new lows.
http://www.theregister.co.uk/2017/02/17/linx_snoopers_charger_gagging_order/
Sinking to new lows.

Some time back, I wrote a post listing the steps required to migrate passwords stored in Chrome to Firefox.
That post was a bit convoluted, so this post is hopefully an improvement! My intention is to make this process as simple, and reliable, as possible. To succeed, you will need:
chrome://flags/#password-import-export…then hit enter.
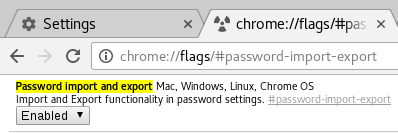
In the option that is highlighted, Select Enabled and then Relaunch.
# Generated by Password Exporter; Export format 1.0.4; Encrypted: false
When pasting, you may be prompted to select the data format. Select “Unformatted Text” in the list and click OK. We are ok with overwriting other cell contents, so “OK” that. Note, you may need to separate out the headings into columns, left to right.
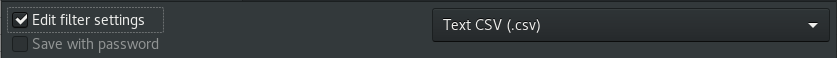
"# Generated by Password Exporter; Export format 1.0.4; Encrypted: false",,,,,,
Delete the leading ” and trailing “,,,,,, from that line.
Secondly, do a Find/Replace on double-commas (,,) making them ,””, (with two quotes inserted) instead. You may need to perform this Find/Replace twice. Now save the file again.
Free software such as Linux is great at many things, including keeping your data very safe. That is, if you are in relative control of it yourself.
Linux is also used by the likes of Google, Facebook, et al., not to mention most western governments. In fact, its flexibility, suitability and cost-effectiveness means it’s pretty much there, in most pieces of consumer electronic equipment, plus any networking kit employed in telephone exchanges and data centres, through to the end points – the receiving servers which constitute “the cloud”.
Its use and application is rich and strange: sometimes in your interests, and often, arguably, not so. But whether you’re a Linux/UNIX, Windows or Mac user, taking care of your own data is vital for a life of value!
Is it possible to retract data that you previously opted to store online, and be confident that cloud service providers no longer keep it stashed somewhere? There are two responses to this:
Let’s assume for a moment that “yes” is, by far, the prevailing truth. “Yes”, data which I previously uploaded was properly deleted when I deleted it, and an online service provider no longer has any copy, nor any meta data about my data (ok, I’m laughing now).
“there are many ways in which you can protect your data, and protect your privacy”
Many of us have done it: uploaded photos to Google Photos, posted images or event information to Facebook, shared our location on Twitter, set up an account on … well, the list goes on. But forgetting the “privacy” policy of such entities, just for a second (well, ok then – it’s not that easy to put aside “We store data for as long as it is necessary to provide products and services to you and others”, but even so!!), there are many ways in which you can protect your data, and protect your privacy. It starts with a little effort and time.
Rome wasn’t built in a day, and neither is your data security. For example, consider the following:
A friend of mine recently lost years of pristine digital photos due to a failure of company equipment (“the company laptop”) and because he hadn’t backed them up to a secondary device – even though he had one of sufficient capacity in his possession!
Don’t let this be you! Get a routine in place for backing up. Even if it’s only monthly, usually cameras and phones have enough capacity to store a month’s worth of shots.
A safe location can be anywhere. You don’t have to get a fireproof safe – although I’m not saying don’t! But if you backup your personal data at home, try not to keep your backup at home. A USB drive costs so little these days, that it’s the perfect medium for backing up photos and then taking it to work and locking in your desk drawer.
Encrypting your data is always a good idea for a removable storage device, provided you can easily remember a strong password. Although the ease of managing encrypted removable storage varies between operating systems (note, it is very easy to encrypt data on GNU/Linux).
A backup is no good if you can’t restore files from it. Luckily, with a simple backup process you can easily monitor and validate that your backups have occurred successfully. If you are confident that your system backups work ok, do another one. Then store. Wash, rinse, repeat.
By setting a rule for yourself to back-up your own data, you won’t become so dependent on cloud services for backing up your photos.
Common objections to keeping data off the cloud include the oft-argued (but ill-conceived) notion that it’s free of cost. Let’s just examine this for a brief moment:
The value of your “free” data storage is in the metadata that is stored with it. Tied to your user account (that same user account you might use to log in to other services, signifying your activity at other times even when not using the primary service…) is data – in the form of metadata – that describes it quite clearly.
That photo which was kindly synced to your cloud provider’s account will contain data, like:
If I am a massive indexing engine and I start aggregating and analysing these data, I will be able to determine some interesting trends:
we are now at a stage where it is easier to get a phone, and rely on Facebook for photo storage
Some people I know seem apathetic towards online security, and yet suspicious towards cloud service provider’s intentions too. Perhaps we are now at a stage where it is easier to get a phone, and rely on Facebook for photo storage, than to “bother” seeking alternatives. “The answer is not readily to hand, so let’s move on.”
The problem with systems is that they need parameters. Do a search on something, somewhere, and you’ll be sure to see ads and sponsored links of that thing, somewhere else. This is, and has been for a while, the new internet “norm”.
Breaking out of this “think, search (hunger); feed (consume with contextual data)” lifestyle has been described as the “search bubble”. A self-fulfilling data management and presentation matrix based on your lifestyle habits.
By adopting a simple routine such as taking care of your own data and not subscribing religiously to online services, it’s possible to find not only more sanctity in life’s unique moments, but also more richness from the due consideration of others. Where people know you a little less, and are curious to know you a little more.
I was lucky to have spotted a recent social media post, alerting me to showings of CITIZENFOUR in London over the past weekend. CITIZENFOUR, in case you are not aware, is a film made by celebrated filmmaker Laura Poitras (Praxis Films), who accompanied journalists Glenn Greenwald and Ewan MacAskill to Hong Kong to interview Edward Snowden in the summer of 2013.
My partner and I took a train to Wimbledon. It was an uncharacteristically warm day, summer-like in all regards except the browning of the leaves. The trees looked tired as we marched along to the station; we weren’t missing this film for anything.
In contrast to the anticipation building up inside of me, waiting to see this film, Wimbledon itself was very ordinary. People going about their normal lives. Appetizing whiffs of just-cooked food were wafting over from the market stalls. Traffic was permanently in a hurry with barely any regard for pedestrians’ safety. And the shoppers held an equally high regard for the traffic too, voluntarily stepping out in front of anything coming.
And the shoppers …
voluntarily stepping out in front of anything coming.
The matinée showing at the bijou HMV Curzon cinema was starting just after lunch. I wanted to get there early so that, in anticipation of the queues, we would be assured of a good seat. When picking up our tickets, we spoke to a member of staff behind the bar/counter about the expected numbers.
Staggeringly, four seats had been booked. Including ours. Citizens: four.
To my slight relief, more than four people eventually turned up and attended the showing. Twenty, maybe. Perhaps thirty, tops. In a 110-seat room. And they were comfortable seats too. The best you’d find in any cinema, with lots of leg room and deep, comfortable cushions.
After reading Lawrence Lessig’s blog post of his recent cinema outing in Cambridge, Massachusetts, with 500 movie-goers attending their picture house, I wondered how there could be such disparity across the pond. For us, there was no line to stand in before entering, and perhaps adding insult to injury, our tickets were not even checked by a member of staff when we walked in to pick our (unallocated) seats.
Perhaps it was the over-air-conditioned screen that turned people away. Considering that outside it was the very end of the British summer and we saw temperatures of 20 deg C, inside was another story altogether. We were lucky if it was more than 14. But I don’t think this was the reason for the poor turn-out; any evidence of forward-thinking would surely have improved the attendance?
What does this say about continued British apathy towards such fundamental issues?
A somewhat senior lady who attended the film, mentioned to me on her way out, “I don’t think I meant to come and see that. I thought it was something else.” Citizen Kane, perhaps? I hope she wasn’t one of the original four who bought in advance…
Perhaps people felt it was a story already told. In some ways it was – but arguably, in many ways the whole story had not been told until now. A couple of reveals towards the end of the film were new information to me. Stuff I wasn’t aware of, from reading the Snowden book.
I am glad that a healthy number of people in the US are curious about this subject and decided to explore it further. You might expect this from the residents of Cambridge (Mass.), with its connection to Free Software and socio-political activism, and well done to them.
So, a quick glance at the population numbers of both areas provides some fairly meaningless stats on which to close.
Cambridge’s popn = 107,000 or so. Wimbledon’s: around 60,000. Roughly speaking, for every 214 residents in Cambridge, one person attended Saturday’s matinée there. Only one person of every 3,040 in Wimbledon managed the same feat. What does this say about continued British apathy towards such fundamental issues?
I am left feeling that provided Centre Court and strawberries are always available, Wimbledon won’t care much. Unless, of course, someone personally has an infraction with the law, as a result authoritarian paranoia. Then, perhaps, it might fill a column in page 7 of the local rag. Residents might even chat about this at a local pub, in-between opinions on the state of the brew.
But to complain against wrongdoings is normal. It’s human nature to focus on the oppressors rather than the oppressed. Luckily, for us, in respectable communities there still burns a glimmer of hope that sense may prevail.